Thinking of combining a Virtual Private Network (VPN) service with a Smart DNS service? If you'll be running both services on the same device, before you leap forward with your plans it's wise to make sure you understand the pros and cons of various combinations of them. I personally favor privacy over convenience. Regarding Smart DNS and VPN services, that means signing up for each service with a seperate provider. Keeping them separated means there is no chance a single entity will have access to all your related online behaviorial data.
Before we begin, if you are searching for information on Smart DNS solutions only, see DNS Alphabet Soup: Dedicated, Dynamic, Smart.
If you are contemplating a VPN solution only, see Do You Really Need (or Want) a VPN?
If you don't know what you need, see Mitigating Risk: Combining Privacy Services.
There are four (4) possible methods to combine a Smart DNS and VPN on the same device. Typically, these reflect installation and setup on a host or router. Examining the list below, on the surface three of the four approaches can meet this requirement. However, you will need to dig deeper to decide which approach will be the best fit for you. Let's examine the caveats of each strategy.
- Single provider: Smart DNS + VPN combined in a single package (geo-unblocking all the time)
- Smart DNS over VPN only
- Separates: Smart DNS over non-VPN + Smart DNS with VPN (two independent Smart DNS accounts; one tethered to VPN)
- Secure VPN: VPN + Smart DNS content over non-VPN connection
Option 1: Single Provider - The Simple Solution
Purely from a privacy perspective, this is the only option I cannot recommend in good conscience. However, for many users this is the one that makes the most sense. If you're not already using a VPN and have no interest in one, this path is for you.
Switching your DNS server over to the Smart DNS service provider's has the benefit of simplifying normal Internet use and circumventing geo-blocked content. It doesn't get any easier than that.
Risk: When combined through a single service, a provider has the capability to monitor a significant portion of your behavior and internet traffic by mapping your VPN behavior to your DNS queries. It is a better practice to separate those functions between different organizations, so that all your metadata is not under one umbrella.
Even if a provider offering both services reassures you they are not correlating data on your activity, the fact remains they have the technological capability to do so. Whereas, when different providers are involved, that capability does not exist.
Option 2: Smart DNS Tethered Only to VPN
The concept here is the Smart DNS service is tethered to the VPN connection. In other words, you can only use the Smart DNS service - including its primary role of circumventing geo-fenced content - after you have first connected to your VPN service. This approach comes with some limitations:
- Circumventing geo-blocked content will work through your VPN
- When not connected to your VPN, circumventing geo-blocked content will NOT work
- Your ISP's DNS (or other default DNS service) will be used when NOT connected to the VPN
- Your Smart DNS account must be associated with your outbound VPN address (i.e. not your true IP address)
- Dynamic VPNs will require you to reset your Smart DNS account tethering (to VPN outbound IP address) every time you reconnect to the VPN
Those last two points are very important and merit further explanation. Your "outbound" IP address when connected to a VPN means your outward-facing IP address. That is the IP address the world sees. It is NOT the IP address you connect to in order to initiate the VPN, and it's not your "true" IP address, which is the IP address your ISP assigns to you. There are two types of VPNs when it comes to these external (outbound) IP addresses: static and dynamic. Most VPNs are dynamic, meaning your outbound IP address may change from login to login. Disconnect from the VPN and reconnect to it, and it's likely you will be assigned a different outward facing IP address.
A few VPN service providers offer static IP addresses. If you are considering using a VPN service with a static IP address, make sure you understand which part of the VPN process is static. By "static IP," a VPN provider may be referring to either a fixed IP address to which your device connects to in order to initiate the VPN connection, or it may refer to the outbound side of your VPN connection, which is what the world sees as your device's IP address. For the purpose of this discussion, you would want a static outbound IP address.
Here is a process flow diagram illustrating the process (all IPv4 addresses shown below are fictitious).
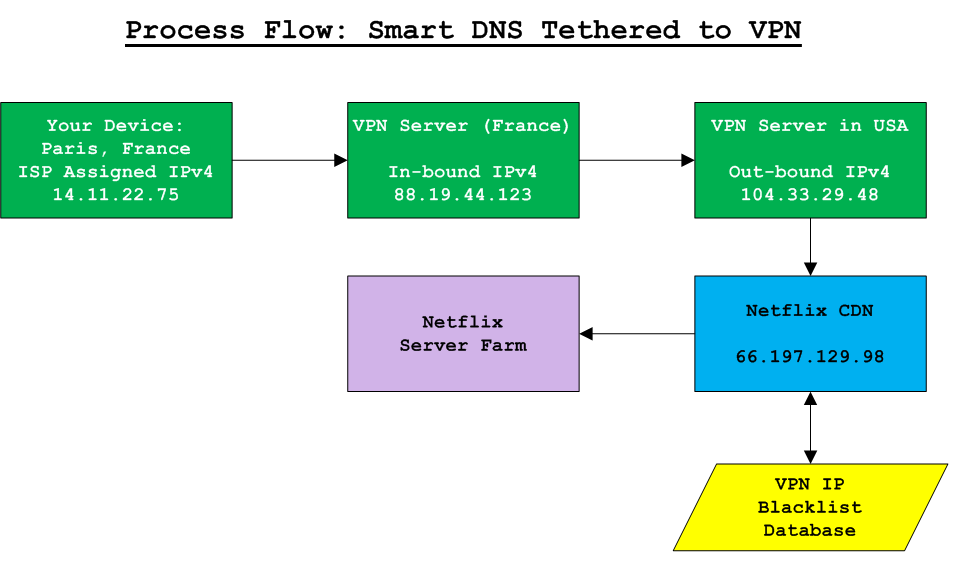
Why not simply use a VPN with an outbound IP address in the same geographic region as the content you wish to access? Smart DNS providers specialize in cirumventing geographic content restrictions. VPN providers do not. Furthermore, it's easier for aggressive content providers to identify VPN servers than proxy servers run by Smart DNS companies, making it easier to block VPNs.
Option 3: Smart DNS Services on Both VPN and non-VPN Connections
This approach requires two (2) Smart DNS accounts and a VPN. The tactic only makes sense if you wish to access geo-restricted content from two (2) different regions at the same time, simultaneously. Otherwise, I recommend avoding this strategy, as it presents the highest operating cost and presents the highest risk to data privacy (i.e. being hacked or monitored without your knowledge).
A unique, potential risk of this approach exists when the same Smart DNS provider is used for both accounts.
It is possible a single DNS service provider could correlate metadata between your true IP address (ISP assigned) and your outbound IP address assigned by your VPN service provider. The risk is higher when the user employs static outbound IP addresses from their device, and is exceptionally low when the user's devices utilize dynamic IP address assignments, such as with most VPNs. Regardless, this is a real privacy risk either way and should be duly noted.
Ideally, you should use two different Smart DNS providers, though the practice is not required. The purpose of this approach is to provide access to geo-fenced content regardless of whether you are connected to a VPN or not. This method is generally discouraged due to its complexity and likely inconveniences.
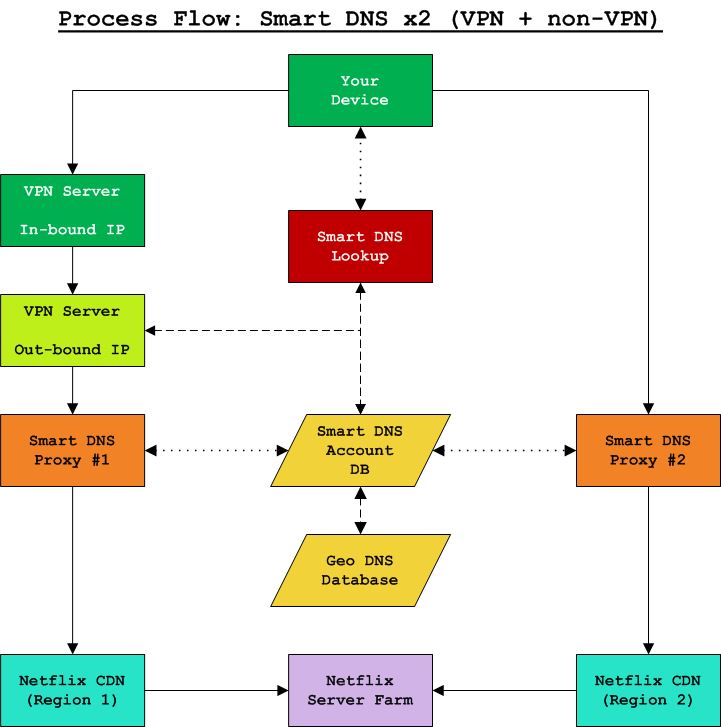
The same limitations and caveats apply to this approach (Option 3) as with Option 2 (Smart DNS Tethered Only to VPN). Most importantly, if you have a dynamic VPN service then every time you initiate a connection to the VPN, you will likely need to re-associate its corresponding IP address registered with the Smart DNS service. Smart DNS services typically maintain a 1:1 correlation between your IP address and the Smart DNS service. If your IP address changes, you must login to your account with the Smart DNS provider and update or re-associate the relationship. In this case, your VPNs current outbound IP address.
The same thing can occur with an IP address assingned by your ISP. With a dynamic IP address service, your IP address is likely to change from time to time (though perhaps not as frequently as your VPNs will change). A change to your local ISP's outbound IP address can be difficult to detect, and will likely occur without prior notification. Furthermore, the Smart DNS service may continue to provide you with normal DNS resolution services. You may not notice there is a problem until you attempt to access geo-restricted content and it fails. This is another subject worth noting when comparing Smart DNS service providers. Ideally, you'll want one where the normal DNS functions continue operating even if there is a disconnect between the association of your IP address and their service. If they don't offer free DNS to the public, then when your DNS lookups begin failing it will be a sign you probably need to login to your Smart DNS account and re-associate your IP address. Note that with a VPN connection, this process is likely to occur every time you connect to the VPN unless you have a static outbound IP address assigned by the VPN service provider.
These are significant drawbacks to this method, and the primary reason why I recommend avoiding this tactic unless you are willing to deal with substantial inconvenience and/or ensure you have static IP addresses (at higher cost).
Option 4: Smart DNS Over Non-VPN Connections Only
This is the most complex setup. It is a tricky reverse implementation of Option 2. The concept is to route all Smart DNS traffic outside your VPN connection, and all other traffic over your VPN. To manage this feat successfully, you will have to segment your network traffic using a Split VPN.
Advanced networking knowledge is a prerequisite of this solution!
You must understand how to setup a Split VPN based on port number, application/program, username, and similar criteria. You need the know-how to split your VPN connection and be able to quantify the traffic you want to exclude from the VPN. If you don't meet that qualification, stop here; this solution is not an option for you.
Want to do this, but don't know where or how to begin?
If you don't already have the requisite knowledge, you may be able to pick it up via this website. Check out the articles in the Virtual Private Networks and Routes and Rules categories. Under the latter, pay particular attention to the articles on Split Gateways, such as my Split Gateway Tutorial. You may need to reference other articles on the site to fully grasp all of the concepts. Remember, this is an advanced topic.
First, identify which of these two situations you're in. Your Smart DNS service provider:
- DOES allow DNS lookups to anyone, whether they have an account or not
- You're in luck; you can branch port 53 TCP/UDP (for DNS) to the Smart DNS all the time
- This means you will always get DNS lookups via the Smart DNS server
- You will still need to branch particular traffic, but it can be done via port only if appropriate
- DOES NOT allow DNS lookups without an account mapped to your IP address
- This is the more complicated scenario
- Split VPN cannot use port number branching alone
- Associate branching port 53 UDP and TCP (DNS lookups) based on username/process
Be conscientous of how you configure your Split VPN/Split Gateway. For example, routing all of your HTTP and HTTPS traffic to a Smart DNS could compromise your intentions for using a VPN in the first place.
The process description below is intended as a guide to keep you on track.
It is not a granular set of steps, as each person's circumstances will require different detailed steps.
If you have the knowledge and capability, you may perform the following steps:
- Attempt to access geo-blocked content and verify you are unable to access it
- Create an account with a Smart DNS service provider
- Sign up for VPN service with a VPN service provider
- Setup your Split VPN such that port 53 TCP and UDP are excluded from the VPN
- Determine if your VPN provider offers a dedicated DNS server (ideally, it will)
- Configure, launch, and connect to your VPN; verify activity while connected works correctly
- Disconnect from your VPN
- If your VPN provider offers a dedicated DNS server, reconfigure your VPN to use it; connect to your VPN again and verify domain names are resolved correctly
- Disconnect from your VPN
- Ensure you are not connected to your VPN and access whatismyip.com (or similar website) with a web browser; verify your true IP address assigned by your ISP
- Login to your Smart DNS provider and configure your account; tether your account to your true IP address assigned by your ISP
- Setup your primary DNS (not via the VPN) to use your Smart DNS service
- Restart your device
- Ensure you are not connected to your VPN and access whatismyip.com (or similar website) with a web browser; verify your true IP address assigned by your ISP
- Attempt to access geo-blocked content and verify you are able to access it
- Connect to your VPN
- Attempt to access geo-blocked content and verify you are unable to access it (via VPN)
If you don't understand what Split VPNs are but would like to learn more, I recommend reading Introduction to Split Gateways, to get you started on the core concepts.

Remember, this isn't just about DNS lookups. This is first and foremost about circumventing geographically restricted content, which requires not only DNS queries, but also going through a Smart DNS proxy server or attempting to use an in-country or intra-regional VPN to access the content.
Non-VPN connections may access geo-restricted content via a Smart DNS service, but VPN connections might not work. Plus, the purpose of this method is to safeguard the integrity of the VPN connection. The trade-off is less convenience and a more complicated networking configuration. As explained above, under Privacy Risks Posed by Smart DNS Services, a Smart DNS service introduces several potential security holes. Those vulnerabilities exist even if the Smart DNS service is accessed via a VPN. The VPN will not protect you from these vulnerabilities, which are a by-product of the Smart DNS process.
It's important to keep in mind how Smart DNS systems function. When attempting to bypass geo-restricted content via a Smart DNS, your device's IP public-facing address must match the IP address the Smart DNS provider has associated with your account. When you make a DNS request via the Smart DNS, your IP address is validated. If it matches an active account, a database look-up is performed. If a region preference has been set in your account and if the DNS request matches a known content provider with multi-regional content delivery networks (CDNs), then the DNS address returned to your device will point to a proxy server that belongs to the Smart DNS network. When you subsequently connect to the IP address provided by the Smart DNS server's DNS lookup, you connect to the proxy server. The proxy server then performs a lookup of your IP address against its account database. The proxy server polls the Smart DNS database to discover your true intended destination (the CDN), and proxies your connection to that final IP destination, establishing your connection.

