Dedicated DNS. Dynamic DNS. Smart DNS. What the heck are these things???
Many consumers get confused between these very distinct services. It's not their fault. I blame the marketing messages of the companies peddling each particular type of product, which are often confusing and don't tell the consumer the whole story one way or another. In this article, I break down their differences and the problem(s) each solves.
I've also written a related article on the pros and cons of combining various privacy services, such as DNS services and VPNs. You'll find that discussion here: Mitigating Risk: Combining Privacy Services.
Contents of this article:
- DNS and How It Works
- Combining DNS Services with a VPN
- What is a Dedicated DNS?
- What is Dynamic DNS?
- What's a Smart DNS?
- What Does a Smart DNS Cost?
- How a Smart DNS Works
- Why Location Matters
- Proxy Servers
- Do You Truly Need a Smart DNS?
- Privacy Risks Posed by Smart DNS Services
- Misguided Marketing Practices
- VPNs
- Routing Network Devices Through a Smart DNS
- Testing Your Smart DNS Service
DNS And How It Works
DNS is an acronym for "Domain Name System." DNS servers translate the name of destinations on a network - such as the Internet - into IP addresses. The job of all DNS servers is translate a domain name (e.g. cnn.com) to an IPv4 or IPv6 address (e.g. 151.101.193.67). They are the magic that allows you to type in "cnn.com" in your web browser and connect to CNN's web servers. Without a DNS server, you would need to know the full IP address and enter it manually. Not only do most people find it easier to remember a name versus an IPv4 or IPv6 address, but many organizations have multiple IP addresses. Which you are directed to depends on a variety of factors, such as spoken language or your physical location.
DNS uses a tiered system. At the top of the tier for the Internet are the root-level DNS servers spread throughout the world that facilitate keeping the whole system running. Below that are multiple secondary tiers that are the workhorse and provide up-to-date IP address translation. The bulk of the workload is handled by this much larger number of secondary and tertiary DNS servers.
DNS also has the ability to share information about the physical location of a record requestor. This feature serves a number of purposes, including the support of validation processes between DNS servers and enhancing end users' experiences through location-aware improvements in routing efficiencies, localization, and content management, among others. In recent years it has evolved into a powerful tool to monitor user behavior and parse content presentation based on location, and ISPs now routinely append location data to DNS record requests. If you'd like to learn more about how it works, see the article DNS Location Data (DNS LOC).
Combining DNS Services with a VPN
Virtual Private Networks (VPNs) are mentioned several times in this article. Why? Commingling any of these DNS services with a VPN impacts all of them. Care and forethought is required to ensure your goals are met, and I caution you to assess the potential impact to your digital privacy and/or ability to accomplish tasks. That's why VPNs in particular are mentioned throughout this article, and additional information is provided below on this important topic.
If you already use a VPN or are contemplating doing so, I strongly recommend reading Mitigating Risk: Combining Privacy Services.
What is a Dedicated DNS?
A dedicated DNS server is a private recursive resolver DNS server. It operates just like any other recursive DNS server, including synchronizing its domain name database with other DNS server types when necessary. Dedicated DNS servers are common with large corporations and VPN service providers. In the case of the latter, they are typically available exclusively to their VPN customers while connected to a VPN server (thus the term "dedicated"). Why is this important? Dedicated DNS servers provide a higher form of privacy protection because all of your DNS queries are localized with the VPN provider. Even a 3rd party monitoring the VPN provider's DNS queries will have no way to determine which device requested any given DNS translation out of all the devices connected to the VPN at that time, nor would they be able to track what all the connected devices were or who they belonged to.
A dedicated DNS may seem unnecessary to many people, since any DNS queries over the VPN will simply be traced back to the VPN server to begin with and not your true IP address. Logging is the most important privacy factor here. If the VPN service does not log any DNS queries then it matters less whether the VPN provider has a dedicated DNS server or not. At that point it becomes a subtle difference which is irrelevant to most people, but if you want maximum privacy then a dedicated DNS should be a consideration in deciding which VPN provider to use. Only a few VPN service providers offer dedicated DNS service.
What is Dynamic DNS?
Dynamic DNS or DDNS is an acronym for Dynamic Domain Name System.
For example, let's say your name is Bob Smith and you've contracted with a DDNS provider called ddns.org, who assigned you the unique domain name of bobs.house.ddns.org. When you are remote from your home, you use that unique domain name as a pointer to your home's automation system.
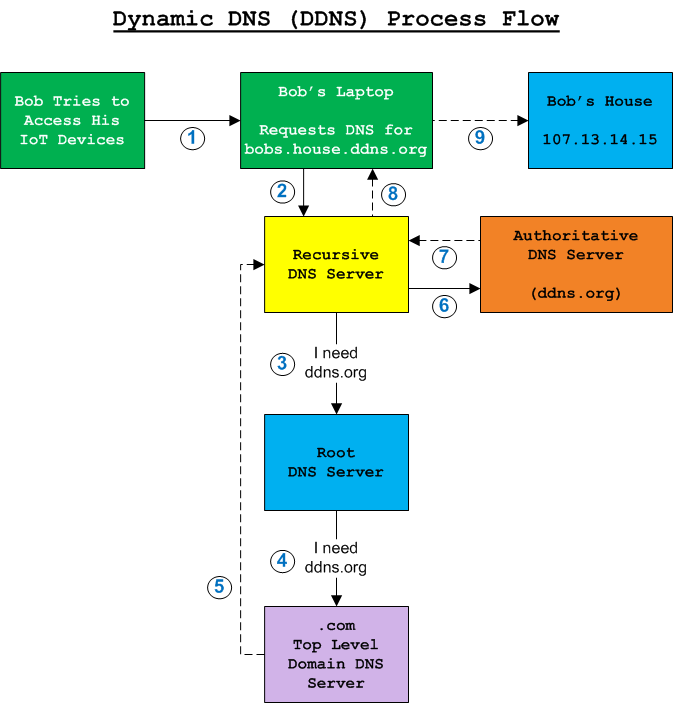
DDNS works just like normal DNS in the sense it involves pointing a domain name to a specific address on the Internet. Normal DNS requires a static IP address. The difference is Dynamic DNS associates a unique domain name with a device when its IP address is not known in advance and/or is subject to change. Thus, the name Dynamic. Therein lies the key to why DDNS is different and why it's a valuable service for many people. Dynamic DNS creates a symbolic link between a device with a dynamic IP addresses and a static domain name).
Dynamic DNS providers assign you a unique domain name, and provide a bridge between it and your IP address. The service maintains a periodic data exchange in order to ensure the associated IP address is accurate. If your IP address changes, the next time the dynamic DNS software installed on your network pings or "phones home" to the provider's servers, their servers will see that your IP address changed, and update their DNS pointers appropriately. When your unique domain name is pointed to by a device on the Internet, the request eventually reaches the Dynamic DNS provider's authoritative DNS servers, which provide a referral to your IP address (the location unique domain name points to, at that moment in time).
What's a Smart DNS?
What is a "Smart" DNS service? Who needs it, who doesn't, what is its purpose? What benefits does it provide? A Smart DNS is a service, and its sole purpose is to enable you to circumvent geographically restricted online content. That's it.
References to the term "Smart DNS" in this document apply to the concept of "smart" DNS services, not a specific service provider.
A Smart DNS is a glorified proxy server, with a twist. It allows you to spoof (fake) your IP address and your physical location. It doesn't change your real IP address, but alters your network traffic such that the destination device you are connecting to perceives you as connecting from an IP address other than your real one. The idea is to fool the server you're connecting to into believing you are physically located in the same geographic region as the destination server.
What Does a Smart DNS Cost?
Here is a random sample of Smart DNS providers and their cost.
| Smart DNS Monthly Cost $USD | |
|---|---|
| Smart DNS Provider | Monthly Rate |
| OverPlay.net | $ 4.16 - 4.95 USD |
| SmartDNSProxy.com | $ 2.08 - 4.90 USD |
| SmartDNS | $ 2.08 - 4.90 USD |
| Unblocker | $ 4.16 - 4.95 USD |
As you can see, there's not a lot of differentiation. The low end of the price ranges represent longer term contract commitments (12 months or more), and the higher prices represent shorter-term agreements (e.g. 1 month). Generally speaking, you should expect to pay less than $5 USD per month for a Smart DNS service. I recommend sampling any service on a trial basis or signing up for just one (1) month to determine if it will work well for you or not. Bear in mind some services retard the scope of their trial, and therefore a trial may limit your experience. The provider should inform you ahead of time if that's the case. Make sure you look for that before signing up for anything. No sense in paying for a test run if you can test the full experience for free. Many Smart DNS providers will even allow you to sign up for a free trial without providing any payment information.
How a Smart DNS Works
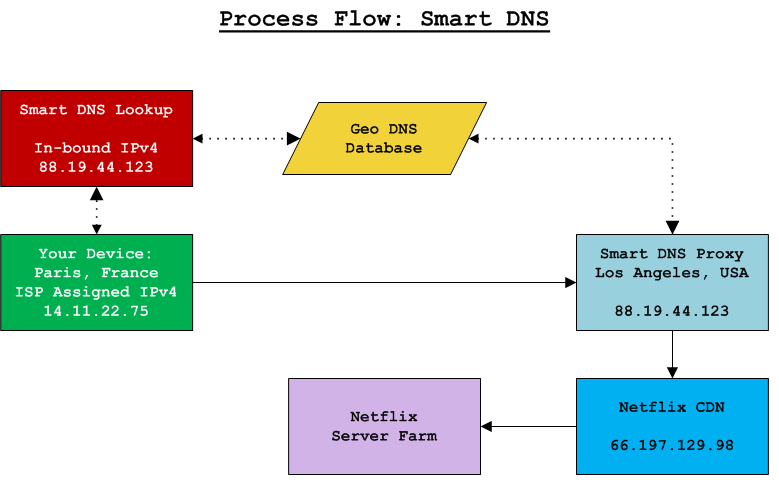
Smart DNS services allow you access to geo-fenced content by tricking the content provider into believing your device is physically located within the content's permitted geographic boundary. The Smart DNS service provider facilitates this facade through two actions. First, when you attempt to access the content provider's Content Delivery Network (CDN) inside the target geographic region, the Smart DNS detects your query and diverts your connection to a proxy server located near the CDN. Second, the proxy server your connection is redirected to forwards your connection to the regional IP address of the CDN. The content provider scans the source IP address of the incoming connection and compares it against a database of geographic coordinates and IP address ranges. In this case, your source IP address appears to be that of the proxy server. Therefore, the connection appears to be in the CDN's local region and is approved by the content provider.
Most Smart DNS providers permit users to modify regional preferences in their account settings (of the Smart DNS account). For example, you could indicate you want to connect to Netflix in the USA while connecting to the Hulu service in Finland. From thereafter, when your device visits netflix.com, it will be redirected to a proxy server in the USA region and you will receive USA based content for Netflix. Meanwhile, when you access hulu.com, you would receive the Finnish content version. The Smart DNS provider maintains a database of regional translations. It processes the appropriate domain name translation, and then processes a DNS lookup for the new domain name. The lookup process is transparent to the end user and does not affect the data embedded inside the connection.
The most important thing to remember is your true IP address assigned by your ISP must match the IP address associated with your Smart DNS provider's account. If it doesn't, your connection will not be redirected and your attempt to circumvent the geofencing will fail.
In order for this system to work, you must pre-arrange a few things or it won't work. The prerequisites are:
- Create an account with a Smart DNS service provider and activate/fund the account as necessary
- Modify your device's DNS settings to point to the address provided by the Smart DNS service provider
- Remove any other DNS server references
- Login to your Smart DNS service account and allow it to auto-detect your legitimate IP address
- Set preferences in your account settings for the Smart DNS service as applicable
- Restart your device
A Smart DNS is pointless for most U.S. residents.
If you need help setting up your network devices to use a Smart DNS, I'll do my best to help guide you. Jump ahead to Routing Network Devices Through a Smart DNS.
Why Location Matters
By default, most Smart DNS services presume you are located outside the U.S. Though pre-configured by default to facilitate access to U.S. based content providers, that doesn't make them totally useless for U.S. residents. However, if you reside in the U.S. and wish to use a Smart DNS service to access content outside the U.S.A., you will need to ensure you sign-up for a Smart DNS service that allows you to modify its target content region. Not all Smart DNS providers offer the same features. Here are some important features to look out for:
- Offers access to content in your desired target region(s)
- Has a configuration tool available allowing you to manually configure target content region(s)
- Ability to configure independent target regions for specific content providers (e.g. Netflix, Hulu)
Smart DNS services are not content providers!
Smart DNS service providers grant you the ability to consume content you are pre-authorized to view (e.g. an active Netflix subscription) via different geographic regions, which may mean you will be able to access licensed content not otherwise available to you based on your current geographic location. You must already have a relationship with the actual content provider or create a relationship with them. The Smart DNS service has nothing to do with the actual content itself. It simply provides you access to content varieties that might not otherwise be capable of accessing. Smart DNS service providers also provide their subscribers with standard DNS lookup services.
Proxy Servers
Let's talk about what proxy servers are, and then continue with how they impact attempts to circumvent geo-fencing.
Proxy servers (sometimes referred to as forward proxy servers or forwarding proxy servers) act as a forwarding or pass-through agent for network connections. A proxy server may inspect and/or modify the data packets, after which it forwards the packet on to its destination IP address. Smart DNS proxies modify the source IP address and swap it for the proxy server's IP address. This has the effect of causing subsequent recipients of the IP packet to believe the proxy server is the origin of the data, and thus accept the proxy server's IP address as the originating IP address. This is similar to one of the behaviors of a VPN server, though there are very significant differences between a proxy server and a Virtual Private Network (VPN) server. I'll go over those differences further down in this article. First, let's be clear on what a proxy server is and isn't.
Risk vs. Reward
Forwarding proxies are a security risk. There are different types of proxy servers. All of them forward your connection to the next upstream router heading toward the packet's final destination. Where they differ is in how they handle the underlying network traffic. Proxy servers generally fall into the following categories, shown in order of least to most invasive:1
- Transparent: Data is passed through without any modification
- Forwarding: Source IP address is masked (changed to look like a different one); data is not scanned and is forwarded to its destination
- HTTP forwarding: Forwarding proxy + XFF applied to HTTP packets only2
- SSL: Transparent proxy that converts unsecured data to secured data, then forwards the encrypted data to its destination; reverses the process for return data
- Caching: a proxy that caches content to speed up web page rendering (normally only found on routers)
- DNS Caching: a proxy that speeds up DNS queries (normally only found on routers)
- HTTPS filtering: deep packet inspection of SSL encrypted content3
1 See The Circle of Trust, below
2 XFF = X-Forwarded-For; explained below, under HTTP Proxy Servers
3 Occasionally found on firewalls, but also common in Man-in-the-Middle attacks; described below under The Circle of Trust
Even with a forwarding proxy in place, it is still possible for your true source IP address to be discovered. Methods exist that are capable of detecting your true IP address. Most streaming products don't. However, if you do run into this problem, your only alternative would be to use a VPN instead. The pros and cons of Smart DNS vs. a VPN for geo-fence circumvention are described further along in this document.
Most proxy servers are type Transparent, Forwarding, or HTTP Forwarding.
Forwarding Proxies
If you're attempting to circumvent geo-fencing, this is the one you want. A forwarding proxy forwards the original traffic without modifying it. The proxy server has the effect of making it look like the data is originating from the proxy server's IP address and not the true source address.
The Circle of Trust
I feel compelled to drive home an important risk factor pertaining to proxy servers. Trust. You must implicitly trust a proxy server, because it has the capability to view and alter your data packets. The classic MitM (Man-in-the-Middle) attack vector often involves proxy servers, because by definition they are authorized to modify packets to begin with. If you don't have direct control over a proxy server, be aware you could be unwittingly putting yourself in harms way.
HTTP Proxy Servers
Most proxies are either transparent proxies or HTTP forwarding transparent proxies. The difference between them is an HTTP forwarding proxy informs upstream routers the IP packet has passed through a proxy server. It also clarifies the original (source) IP address, and appends the proxy server IP address. This information is conveyed to upstream routers via an HTTP header protocol called X-Forwarded-For (XFF). The XFF header maintains a list of the original source IP address, followed by the IP address of every proxy server the packet has passed through (in order). When the packet passes through subsequent proxy servers and already contains an XFF header, they will usually append their IP address to the XFF header. However, this practice is not guaranteed.
While XFF headers are supposed to follow a standard syntax (see RFC 7239), there is no enforcement mechanism (data type or whether or XFF is used properly or not). This is another reason why it's important to fully trust a proxy server.
This "I just came from a proxy server" notification method for HTTP is used frequently in large scale website implementations where servers are performing load balancing between multiple servers, or possibly even co-located servers. If you're managing a server farm, it makes sense to keep track of the original IP address source of the data packet as it ensures message replies are returned to the appropriate IP address.
Proxy Servers and Smart DNS
A proxy server is an integral part of a Smart DNS system. A Smart DNS returns the IP address for the content you want to receive, in the region of the world where you want to receive it. Their only purpose is to circumvent geographic restrictions on content. The proxy server portion of that equation is a necessity as well. It's sole purpose is to disguise the true origin of your IP address. Without that piece of the proverbial puzzle, the content provider could easily perform a reverse look-up on your source IP address and determine you were outside the geographic limits of the content you were requesting and you'd be blocked.
If proxy servers require you to accept some risk in order to attain your goal, why not simply use a VPN? That is certainly an option, though it is not without its own compromises.
Do You Truly Need a Smart DNS?
If your goal is only to circumvent geo-blocking/geographic-based digital content restrictions, a Smart DNS service may be all you need, or it may be pointless. I caution you to consider these factors:
- If you reside in the USA, a Smart DNS service is likely pointless (remember, there is no point in using one unless you want to access content outside your current country or region)
- It uses a forwarding proxy server to disguise your true location, to get around content restrictions based on your device's IP address
- Proxy servers increase your risk of your data being compromised by a malicious actor (especially 3rd party proxy servers you do not control)
- Smart DNS services may reduce your level of privacy
Privacy Risks Posed by Smart DNS Services
Using a Smart DNS is not without risk. There is no free lunch. The primary security risks of using a Smart DNS service are Privacy Risks, DNS Snooping, and MitM (Man-in-the-Middle) attacks.
Unfortunately, anytime you introduce a third party service into your Internet browsing experience, you are adding an element of risk. This is particularly true of online privacy, which as you are likely aware is under assault from a number of angles. So, what does a Smart DNS add to this equation?
- No control over Smart DNS logging
- Proxy server vulerable to MiTM attacks
- Proxy server might log your activity
I've ignored obvious risks, such as if the Smart DNS provider's servers were to be compromised and your DNS history were snooped by a hacker or the possibility of government surveillance of your DNS behavior via a Smart DNS provider. The risks outlined above are less-obvious risks that many consumers contemplating a Smart DNS service are likely unaware of.
Make sure you understand the potential pitfalls of proxy servers before you sign up for a Smart DNS service.
Smart DNS process flow diagram:
Plain Text DNS Vulnerability
DNS queries are sent in plain text (they are not encrypted). Any device en route between your device or router and the DNS server may intercept and inspect DNS traffic, including but not limited to domain names, corresponding IP addresses, the address of the DNS server itself, and your true IP address.
Using a Smart DNS can negatively impact your online privacy. Even if you're not using a DNS server address assigned by your ISP, your DNS traffic can still be intercepted and snooped (viewed) by your ISP, and your ISP is almost undoubtedly doing so. That doesn't change with a Smart DNS. If you want to completely hide your DNS activity, you will need to use a VPN with a private (dedicated) DNS server. That concept is explored later in this article.
Does a Smart DNS increase the risk of privacy invasion? Does it increase the extent to which your privacy is monitored?
By signing up for a Smart DNS service, you are exposing your online activity to a private company that may (and probably will) collect and log your DNS query activity, for whatever reason. In today's world that is the norm. Virtually all ISPs (Internet Service Providers) - and many DNS providers - log your DNS activity. They do this primarily for the purpose of collecting information about you. This information is sold to marketing companies and many of them also use it to serve you relevant advertisements. And finally, they retain this information for record-keeping purposes to comply with data retention laws and policies.
Smart DNS Proxy Server Vulnerability
The area I find of most significant concern is the proxy server concept Smart DNS services rely upon. A forwarding proxy server is employed as part of the Smart DNS geo-fencing mitigation strategy. This is a crucial step, as the whole process behind Smart DNS and geo-restriction circumvention depends upon it. Unfortunately, this process exposes the end user to additional risks. One of the most significant is the threat of a MiTM (Man-in-the-Middle) attack. A MitM attack vector where a hacker compromises a server on the communication path between your device and its destination, such that the hacker is able to view information traversing the compromised server. The hacker will be able to view your source IP address, destination IP address, and the content of your transmission. If that content is not encrypted, all of your connection's information is exposed.
Misguided Marketing Practices
Just like Virtual Private Networks (VPNs), Smart DNS providers frequently extoll fear as a marketing technique to convince users to sign-up for their services. The question is, do these claims overstate related privacy issues and mislead the public? I would say this is often partially the case, but Smart DNS providers don't seem to be riddled with as many scams as VPN providers. As usual the devil is in the details. Here is an excerpt from one Smart DNS vendor's marketing material that is somewhat misleading:
"... your ISP-assigned DNS address (which contains info that can reveal your geo-location)."
Is it true? Mostly. How is it misleading? In my opinion, yes. That statement is factually inaccurate and oversimplifies the matter. DNS traffic can and usually does contain physical location information, however the statement above is misleading because:
- Your ISP does not assign you a DNS address; it assigns you an IP address
- DNS lookups might be performed by servers owned by your ISP, or they might not
- DNS requests can (and often do) contain geo-location data pointing to the origin of the request
- Most ISPs obfuscate the geo-location data embedded in the DNS request; the granularity of your location data is decided by your ISP
Still a Reason for Concern
Now that I've pointed out how some of these companies use fear-mongering as a marketing tactic, I'm going to tell you why you may have cause for concern.
Thanks in part to the proliferation of highly-publicized activities such as doxing and Swatting, most ISPs now take steps to obfuscate the exact physical address of consumer accounts. Even so, the DNS LOC record typically identifies the city, county, or area in which the source IP address is located. This means if a bad actor intercepts your DNS traffic, it's not difficult for them to correlate your DNS LOC record information and with minimal personal details and derive your exact physical location. The more personal information a hacker knows about their target, the easier it is for them to validate its location. DNS LOC data is particularly helpful as it narrows the starting point considerably. For example, imagine you are searching for someone with the last name, "Smith" in the United States. A recent search on the Internet White Pages showed 3.7 million hits for "Smith." Now, imagine you have the last name Smith and a DNS LOC record with longitude and latitude, which you know is approximate. You surmise the target's true GPS location is likely within a short distance of the DNS LOC value. Perhaps 10 miles (that's being conservative btw; most are much closer - 5 miles or less). Now, you are able to narrow your search for "Smith" to a 10-mile radius of the DNS LOC record coordinates. If you also have a first name, you will no doubt come up with at most a few possible locations. So, you can see how easy this is to find someone. Even in spite of an ISP's good intentins to mask their customer's true location, the masking performed by most ISPs is an ineffective strategy given a modicum of additional information in the hands of a hacker.
If any of these facts bother you, consider using a Smart DNS service, VPN service, or both.
VPNs
Want to learn more about Virtual Private Networks (VPNs)? Here is a short list of related topics:
Routing Network Devices Through a Smart DNS
This is a general guideline for how to setup a network host device so its DNS queries are sent through your Smart DNS service provider. If your service provider has given you other instructions, you should try them first. If they don't work or you don't have any instructions, try these.
Routing All Devices Through a Smart DNS
If you want ALL the devices on your local network to use a Smart DNS service and all your devices access the Internet from behind a single router, there is a straightforward way to accomplish this. It's going to be a little bit of work if you've never done this before, but the payoff is you won't need to do it again unless you add another device in the future to your local network or change your router.
- Login to your router's configuration and locate its DNS settings. Change its primary DNS address(es) to point to the DNS server address(es) obtained from your Smart DNS service provider. Any other DNS server addresses may be retained as secondary DNS resolvers or removed.
- Reboot your router.
I recommend retaining a known, good DNS server address in the secondary DNS server position, as backup. If you remove all DNS server addresses except for your Smart DNS providers', if those fail to work for any reason - such as if you have a dynamically assigned IP address from your ISP, and it changes - you will not have any valid DNS server pointers and you won't be able to surf the Internet.
Now, setup each host device on your network. You want to be sure they are getting their DNS resolution through your network's router.
- For each device on your network, access its device settings and locate the network configuration.
- Change the DNS server address(es) to point to your local router's IP address. Remove any other DNS server addresses.
- Restart the device.
Routing Select Devices Through a Smart DNS
Routing only a specific device via a Smart DNS is a similar process to routing all devices on your network, but requires a bit more investigation. The potential gotcha with this approach is if your router forces DNS connections to a particular DNS server. This is uncommon, but possible. Begin by setting up the device(s) you wish to use the Smart DNS server.
This section presumes you have NOT followed the "Routing All Devices Through a Smart DNS" approach described above.
- For each device, access the device settings and locate its network configuration.
- Change its DNS server address(es) to point to the Smart DNS server IP address (or addresses if more than one). Remove any other DNS server addresses.
- Restart the device.
Testing Your Smart DNS Service
How do you know if it works? It's time to test and verify your Smart DNS service is functioning as expected. Attempt to access geographically restricted content and see if it works. If it does not, check the following:
- For each device unable to view the expected content, access the device settings and locate its network configuration.
- Verify its DNS server address(es) point to the Smart DNS server IP address (or addresses if more than one). Remove any other DNS server addresses.
- If you did not change anything on your devices (i.e. everything looked correct), login to your Smart DNS account, verify your account is active, and examine what IP address their system has associated with you.
- Visit whatismyip.com to verify your IP address. Is it the same as the Smart DNS provider's? If not, you need to initiate their validation process again to associate the correct IP address. This problem can occur if your ISP assigns dynamic IP addresses and your ISP-assigned IP address has recently changed.
- If the steps above did not solve your problem, login to your router's configuration and locate its DNS settings. Observe whether or not there is a setting that overrides DNS requests from your network devices and forces them to use the router's DNS settings. If you find such a setting, disable it.
- If you changed any settings on your router, reboot it.
- If you did not change any router settings, login to the gateway router for your ISP.
- Find the gateway router's network configuration settings and locate its DNS settings. Observe whether or not there is a setting that overrides DNS requests from your internal network devices and forces them to use the ISP's DNS settings. If you find any such settings, disable them if possible. If you cannot disable them, determine if you can edit them. If you can edit them, consider changing them to the Smart DNS server IP address(es). Note this will force ALL (non-VPN) connections from your network to use the Smart DNS, which may be undesirable for one reason or another (depending on your goals).
- If you changed any settings on the gateway router, reboot it.
Hopefully, one of those steps will get you up and running. If none of those solutions solve the problem, you're running out of options. Contact your ISP and inquire if they are doing anything to force your DNS queries to a particular server. They shouldn't be, but these days I would not put it past any ISP to intercept obvious DNS traffic and route it through their own servers. If they do, inquire if they will discontinue the practice for your account. If not, I would recommend you change ISPs.

